AppDefender for AWS Lambda
AppDefender can be added to your new or existing Lambda functions via a simple configuration change, with no need for code changes or deployments.
Prerequisites
- a license key. Get one if you don't have one already.
- information about your AWS Lambda function:
- AWS region, e.g.
us-west-1 - Lambda instruction set architecture, e.g.
x86_64orarm64. If you are not sure, it's most likely the defaultx86_64 - Note: AppDefender is supported for all the Amazon Linux 2 and Amazon Linux 2022 runtimes, but not those on Amazon Linux 1. Reference our support Matrix for more details.
- AWS region, e.g.
- permission to modify AWS Lambda environment variables and layer. Note: no new code deployment is necessary
Configure AppDefender
- add the
Extrinsec-Appdefenderextension as a layer to your Lambda, using the following ARNarn:aws:lambda:<AWS_REGION>:201476247173:layer:Extrinsec-Appdefender:<EXTENSION_VERSION>- replace
<AWS_REGION>with your region (e.g.us-east-1) and<EXTENSION_VERSION>with the latest published version of our layer for your region, e.g.arn:aws:lambda:us-east-1:201476247173:layer:Extrinsec-Appdefender:5 - replace
Extrinsec-AppdefenderwithExtrinsec-Appdefender-arm64if you are using arm64 runtimes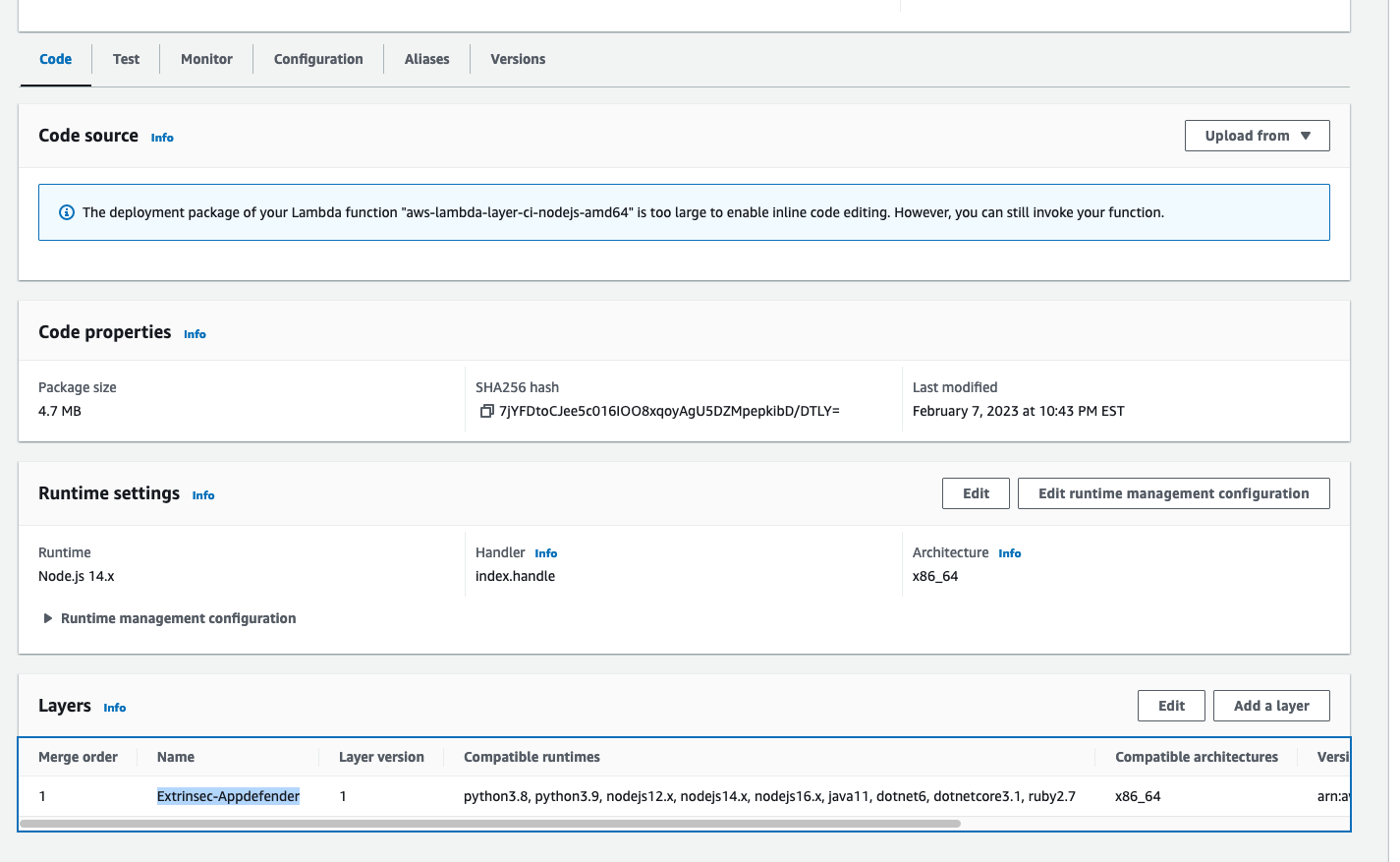
- add the following environment variables to your Lambda
ES_LICENSE_KEY=your license keyES_POLICY_GROUP_NAME=name of your policy group, useobserveAll.abilityif you have a temporary license keyAWS_LAMBDA_EXEC_WRAPPER=/opt/extrinsec-appdefender.sh, (this enables AppDefender)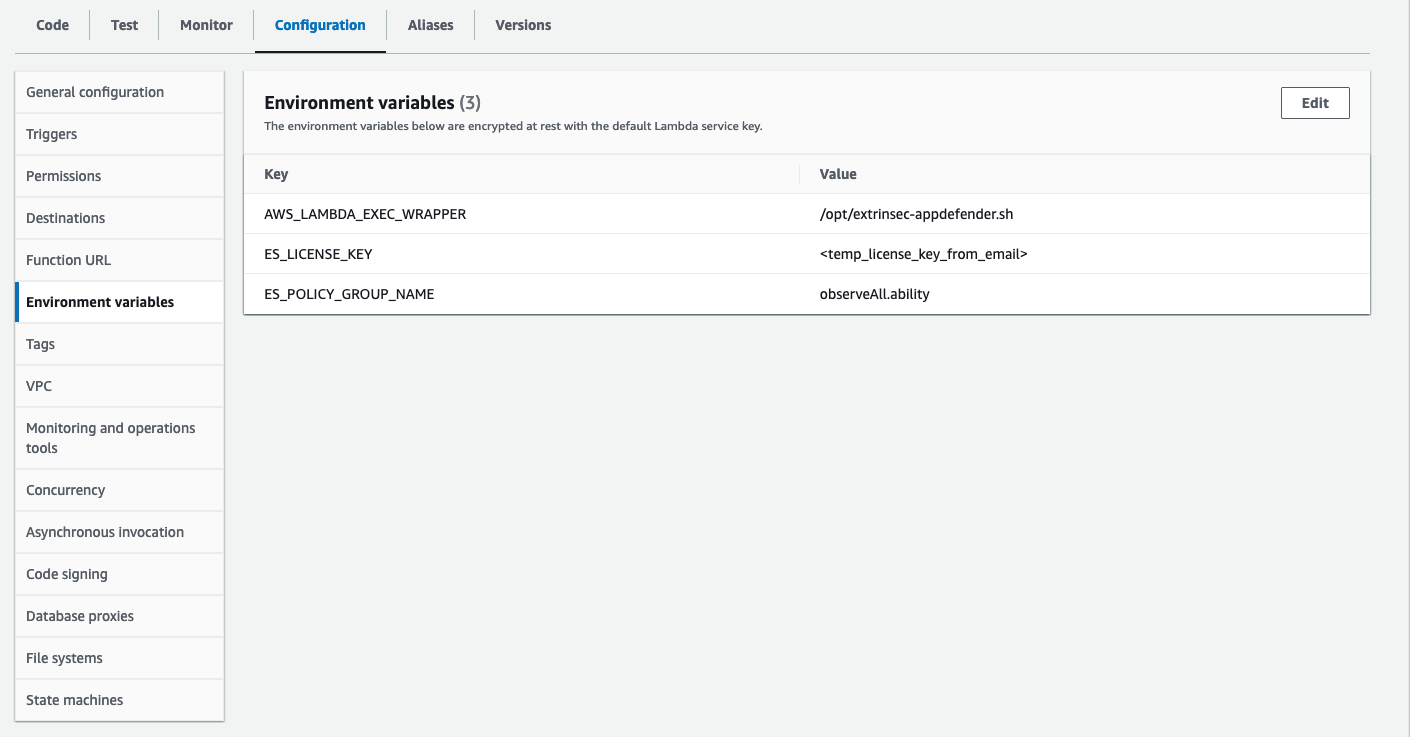
- see AppDefender in action in your CloudWatch logs or any logging service of your choice, e.g.

Configure Policy Groups
- if you have a registered account, then you can create and edit your own policy groups
- if you have a temporary license key, then please use either the
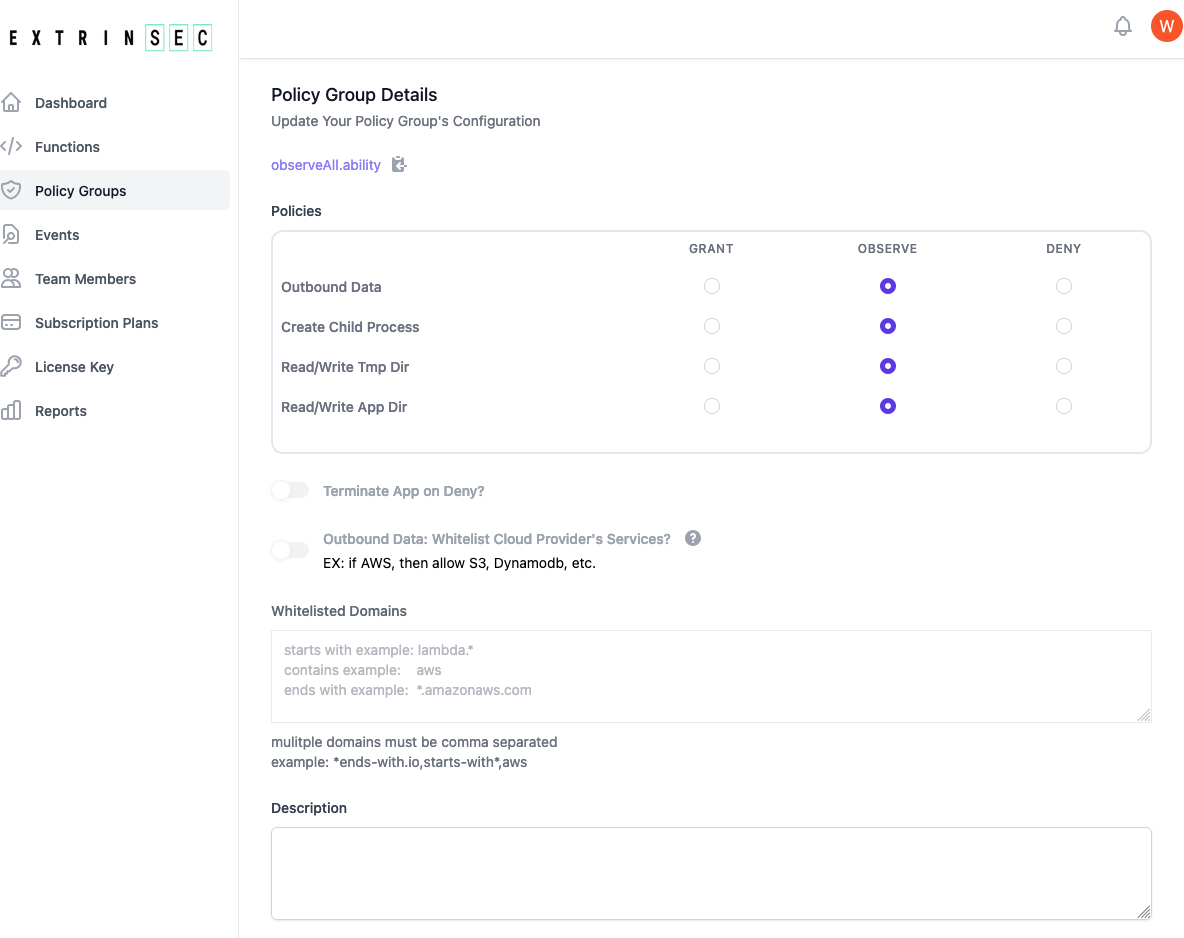
observeAll.abilitypublic policy group or register for a free account and create your own custom policy group - each policy group contains instructions for AppDefender during execution:
- Grant, Observe, or Deny access to any combination of the following:
- outbound network traffic from the serverless function/application process
- read/write on the /tmp/ or application directories
- create/spawn child processes
- whether to terminate serverless serverless function/application execution for any deny event
- whether to allow all cloud provider traffic if outbound data is set to deny. Note: you must upgrade your free plan in order to enable this feature
- this is cloud provider specific, so if you are running on GCF and this option is set, all Google Cloud traffic would be allowed
- a custom list of allowed domains if outbound data is set to deny
- domain names are matched as contains by default, e.g.
stripe(contains) would matchstripe.comas well asm.stripe.com - wildcards can also be used, e.g.
*.amazonaws.com(end with) orlabmda.*(starts with) - multiple domains are comma separated
- AppDefender performs DNS resolution to act on all IP addresses matching the specified domain names
- domain names are matched as contains by default, e.g.
- A optional description field for you to document the purpose or other details of the policy group
- Grant, Observe, or Deny access to any combination of the following:
- create as many policy groups as you have unique needs. There is no limit on how many policy groups you may have
- once a policy group is updated, the changes are automatically picked up by any AppDefender protected application during its next start/restart
View Your Functions and Events
- if you have a registered account, you can view all your functions/applications in the dashboard automatically, as reported by AppDefender. The cloud provider information, as well as the language runtime and policy group used, are all shown
- you can also view all events as detected by AppDefender in the dashboard
- each event is a observe or deny occurrence as outlined in the section above. Note: grant policies don't generate events
- events are reported by the AppDefender to your dashboard in real time. You can use event reporting to better understand the actions of your functions/applications, as well as inform you on how to better customize your policy groups
- events are kept for different durations depending on your current pricing plan