AppDefender for Zoho Catalyst Functions
Prerequisites
- a license key. Get one if you don't have one already.
- information about your Zoho Catalyst function:
- Catalyst Functions runtime, e.g.
Nodejs 16 - AppDefender is supported on Catalyst Functions Node.js and Java runtimes. Reference our support Matrix for more details.
- Catalyst Functions runtime, e.g.
- permission to deploy a new version of your function with AppDefender enabled
Configure AppDefender
Install and import library
Select the language runtime and install the AppDefender package as a dependency in your Catalyst function. Make sure to replace the version numbers below with the latest.
Node.js
- install the AppDefender npm package, which updates the
package.jsonfile. Include the node_modules directory in your deployment.package.json{
"main": "index.js",
"dependencies": {
...
"@extrinsec/appdefender": "latest"
}
} - import AppDefender in your execution main script, e.g.index.js
const appdefender = require('@extrinsec/appdefender');
Java
download the AppDefender Java package, and include the jar files in the
libdirectory of your function project.$ mvn -DgroupId=com.extrinsec -Ddest=./lib/appdefender-0.4.1.jar -DartifactId=appdefender -Dversion=0.4.1 dependency:getimport and enable AppDefender in the execution main method (specified in
catalyst-config.json), e.g.MyFunction.javaimport com.extrinsec.AppDefender;
// enable appdefender in the handler function
AppDefender.enable();
Set environment variables
add the following environment variables to your serverless function/application
ES_LICENSE_KEY=your license keyES_POLICY_GROUP_NAME=name of your policy group, useobserveAll.abilityif you have a temporary license key
Invoke function
- Invoke your function and seee AppDefender in action in your logs
Configure Policy Groups
- if you have a registered account, then you can create and edit your own policy groups
- if you have a temporary license key, then please use either the
observeAll.abilitypublic policy group or register for a free account and create your own custom policy group - each policy group contains instructions for AppDefender during execution:
- Grant, Observe, or Deny access to any combination of the following:
- outbound network traffic from the serverless function/application process
- read/write on the /tmp/ or application directories
- create/spawn child processes
- whether to terminate serverless serverless function/application execution for any deny event
- whether to allow all cloud provider traffic if outbound data is set to deny. Note: you must upgrade your free plan in order to enable this feature
- this is cloud provider specific, so if you are running on GCF and this option is set, all Google Cloud traffic would be allowed
- a custom list of allowed domains if outbound data is set to deny
- domain names are matched as contains by default, e.g.
stripe(contains) would matchstripe.comas well asm.stripe.com - wildcards can also be used, e.g.
*.amazonaws.com(end with) orlabmda.*(starts with) - multiple domains are comma separated
- AppDefender performs DNS resolution to act on all IP addresses matching the specified domain names
- domain names are matched as contains by default, e.g.
- A optional description field for you to document the purpose or other details of the policy group
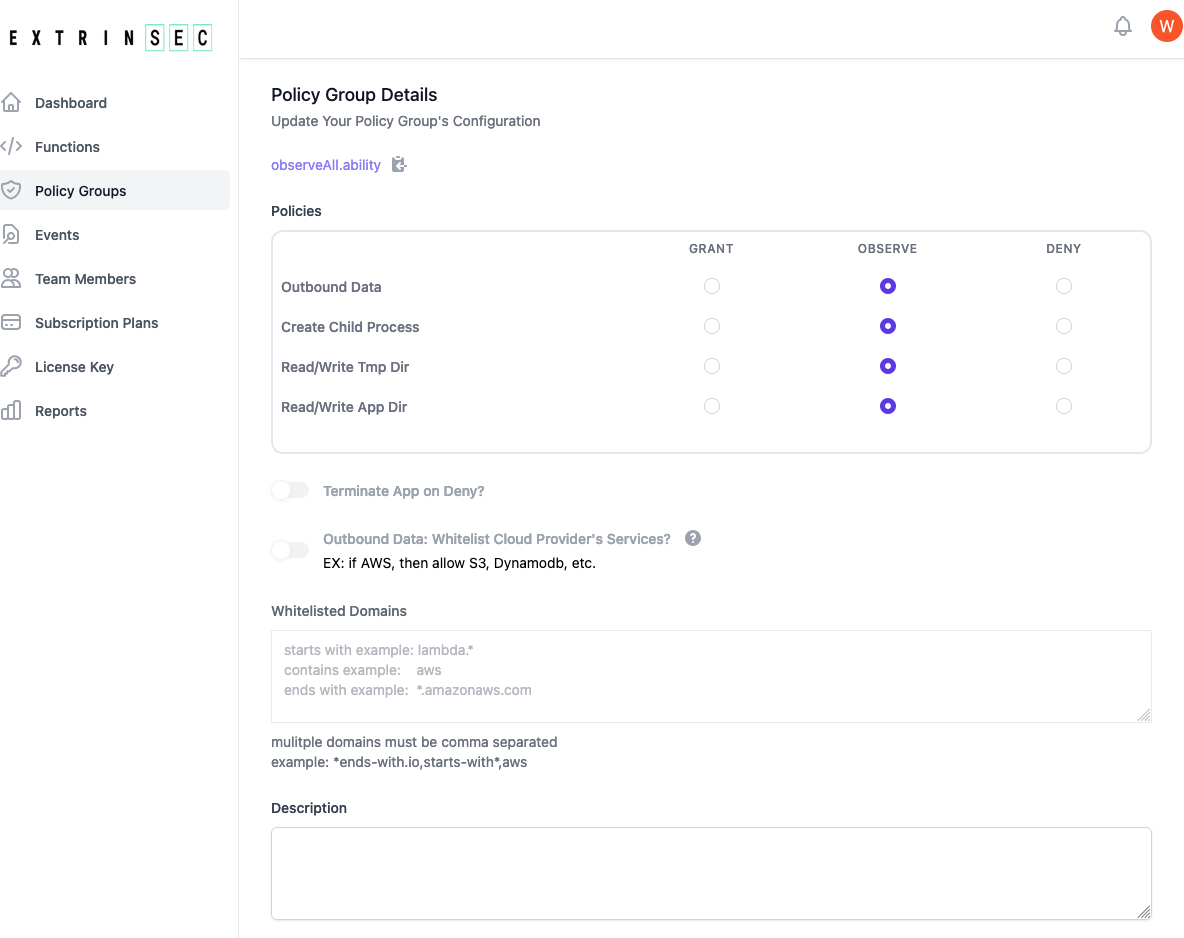
- Grant, Observe, or Deny access to any combination of the following:
- create as many policy groups as you have unique needs. There is no limit on how many policy groups you may have
- once a policy group is updated, the changes are automatically picked up by any AppDefender protected application during its next start/restart
View Your Functions and Events
- if you have a registered account, you can view all your functions/applications in the dashboard automatically, as reported by AppDefender. The cloud provider information, as well as the language runtime and policy group used, are all shown
- you can also view all events as detected by AppDefender in the dashboard
- each event is a observe or deny occurrence as outlined in the section above. Note: grant policies don't generate events
- events are reported by the AppDefender to your dashboard in real time. You can use event reporting to better understand the actions of your functions/applications, as well as inform you on how to better customize your policy groups
- events are kept for different durations depending on your current pricing plan