AppDefender for Python
Prerequisites
- a license key. Get one if you don't have one already.
- install the AppDefender Python package and include in your project (requirements.txt), e.g.
python3 -m pip install appdefender - Note: see the cloud provider specific documentations for more specific details
Configure AppDefender
- import AppDefender (inside your entire application for the best protection), e.g.
import appdefender
add the following environment variables to your serverless function/application
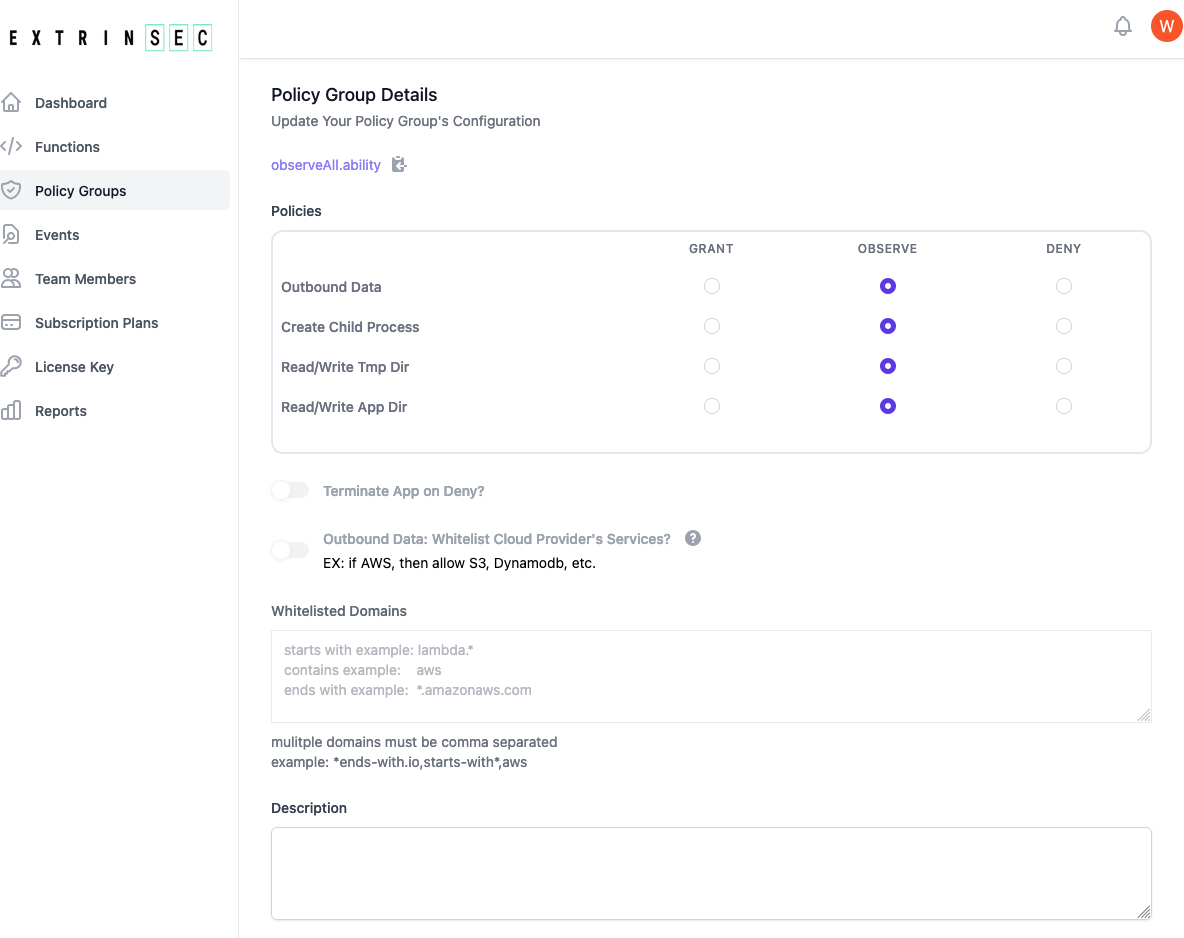
ES_LICENSE_KEY=your license keyES_POLICY_GROUP_NAME=name of your policy group, useobserveAll.abilityif you have a temporary license key
Add the environment variable
ES_APP_NAME=<your unique application name>if running inside a container
Configure Policy Groups
- if you have a registered account, then you can create and edit your own policy groups
- if you have a temporary license key, then please use either the
observeAll.abilitypublic policy group or register for a free account and create your own custom policy group - each policy group contains instructions for AppDefender during execution:
- Grant, Observe, or Deny access to any combination of the following:
- outbound network traffic from the serverless function/application process
- read/write on the /tmp/ or application directories
- create/spawn child processes
- whether to terminate serverless serverless function/application execution for any deny event
- whether to allow all cloud provider traffic if outbound data is set to deny. Note: you must upgrade your free plan in order to enable this feature
- this is cloud provider specific, so if you are running on GCF and this option is set, all Google Cloud traffic would be allowed
- a custom list of allowed domains if outbound data is set to deny
- domain names are matched as contains by default, e.g.
stripe(contains) would matchstripe.comas well asm.stripe.com - wildcards can also be used, e.g.
*.amazonaws.com(end with) orlabmda.*(starts with) - multiple domains are comma separated
- AppDefender performs DNS resolution to act on all IP addresses matching the specified domain names
- domain names are matched as contains by default, e.g.
- A optional description field for you to document the purpose or other details of the policy group
- Grant, Observe, or Deny access to any combination of the following:
- create as many policy groups as you have unique needs. There is no limit on how many policy groups you may have
- once a policy group is updated, the changes are automatically picked up by any AppDefender protected application during its next start/restart
Best Practices
- know your application's access patterns by running AppDefender in observe mode initially. Then use a custom policy group with the minimum permissions
- if using SSR frameworks, make sure the environment variables are available for the backend runtime