AppDefender for Azure Functions
Prerequisites
- a license key. Get one if you don't have one already.
- information about your Azure function:
- Azure Functions runtime, e.g.
C# .NET 6.0 - AppDefender is supported on runtime version 4.x for Linux only in languages C#, Javascript, Java and Python. Reference our support Matrix for more details.
- Azure Functions runtime, e.g.
- permission to deploy a new version of your function with AppDefender enabled
Configure AppDefender
Install and import library
How you include the AppDefender packages depends on the development and deployment environments you use. Typically you would install the AppDefender dependency locally first, but remote or CI/CD options are also supported. Sample installation steps are shown below. Make sure to replace the version numbers below with the latest.
Node.js
- install the AppDefender npm package, which updates the
package.jsonfile. See Azure documentation for more details.package.json{
"main": "index.js",
"dependencies": {
...
"@extrinsec/appdefender": "latest"
}
} - import AppDefender in your function entry point script/scriptFile, e.g.index.js
const appdefender = require('@extrinsec/appdefender');
Python
- install the AppDefender Python package, which updates the
requirements.txtfile. See Azure documentation for more details.requirements.txtappdefender - import AppDefender in your function entry point script/scriptFile, e.g.main.py
import appdefender
Java
update your project configuration file for your build system to include the AppDefender Java package. See Azure documentation for more details. Sample Maven pom.xml file shown below:
pom.xml<dependencies>
<dependency>
<groupId>com.extrinsec</groupId>
<artifactId>appdefender</artifactId>
<version>0.4.1</version>
</dependency>
...
<dependencies>import and enable AppDefender in your function @FunctionName's entryPoint method, e.g.
MyFunction.javaimport com.extrinsec.AppDefender;
// enable appdefender in the entryPoint method
AppDefender.enable();
C#
update your project configuration file to include the AppDefender Nuget package. See Azure documentation for more details.
MyProject.csproj<Project Sdk="Microsoft.NET.Sdk">
...
<ItemGroup>
<PackageReference Include="AppDefender" Version="0.4.1">
<IncludeAssets>all</IncludeAssets>
</PackageReference>
</ItemGroup>
</Project>import and enable AppDefender in your function entry point (decorated with
FunctionNameattribute), e.g.MyFunction.csusing AppDefenderSDK;
// enable appdefender in the handler function
AppDefender.enable();
Set environment variables
add the following environment variables to your serverless function/application
ES_LICENSE_KEY=your license keyES_POLICY_GROUP_NAME=name of your policy group, useobserveAll.abilityif you have a temporary license key
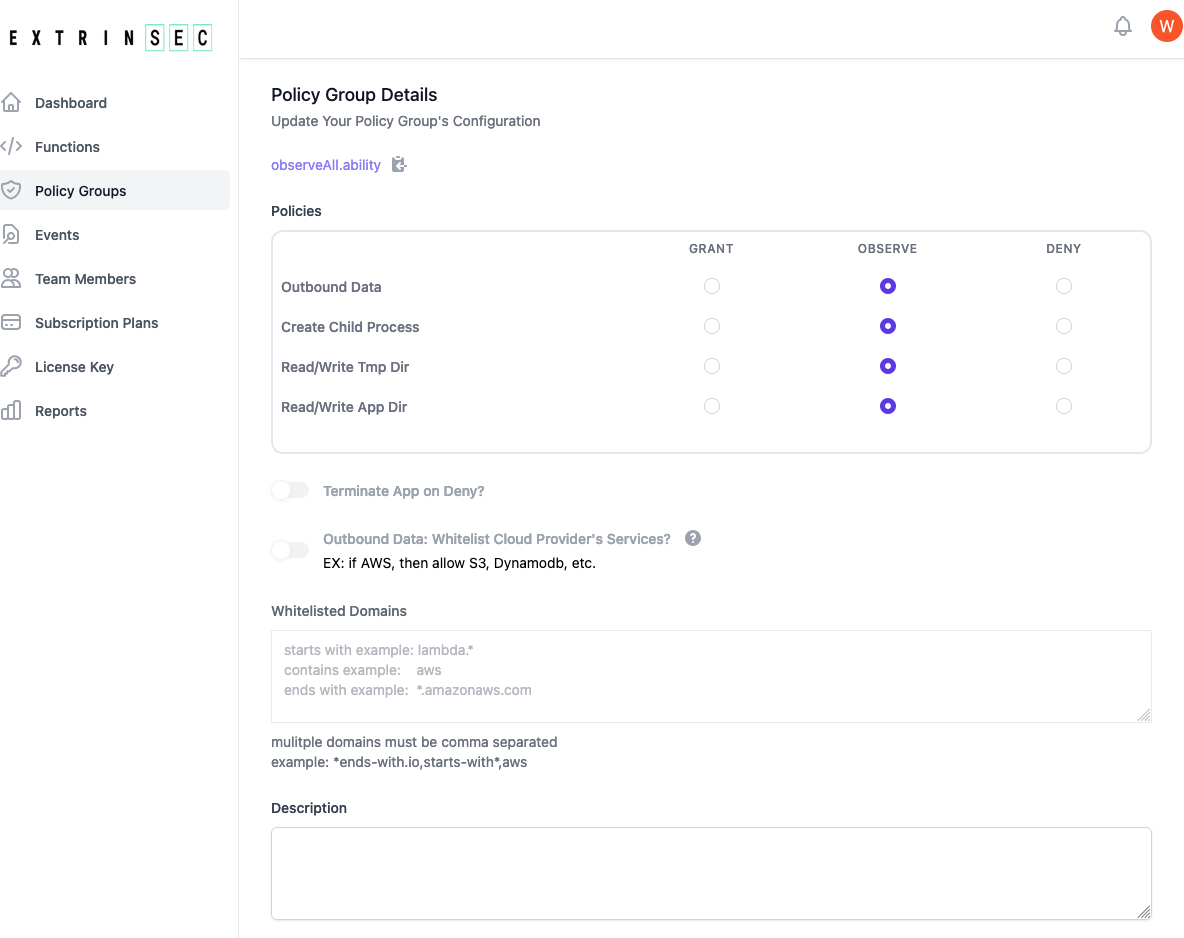
Configure Policy Groups
- if you have a registered account, then you can create and edit your own policy groups
- if you have a temporary license key, then please use either the
observeAll.abilitypublic policy group or register for a free account and create your own custom policy group - each policy group contains instructions for AppDefender during execution:
- Grant, Observe, or Deny access to any combination of the following:
- outbound network traffic from the serverless function/application process
- read/write on the /tmp/ or application directories
- create/spawn child processes
- whether to terminate serverless serverless function/application execution for any deny event
- whether to allow all cloud provider traffic if outbound data is set to deny. Note: you must upgrade your free plan in order to enable this feature
- this is cloud provider specific, so if you are running on GCF and this option is set, all Google Cloud traffic would be allowed
- a custom list of allowed domains if outbound data is set to deny
- domain names are matched as contains by default, e.g.
stripe(contains) would matchstripe.comas well asm.stripe.com - wildcards can also be used, e.g.
*.amazonaws.com(end with) orlabmda.*(starts with) - multiple domains are comma separated
- AppDefender performs DNS resolution to act on all IP addresses matching the specified domain names
- domain names are matched as contains by default, e.g.
- A optional description field for you to document the purpose or other details of the policy group
- Grant, Observe, or Deny access to any combination of the following:
- create as many policy groups as you have unique needs. There is no limit on how many policy groups you may have
- once a policy group is updated, the changes are automatically picked up by any AppDefender protected application during its next start/restart
View Your Functions and Events
- if you have a registered account, you can view all your functions/applications in the dashboard automatically, as reported by AppDefender. The cloud provider information, as well as the language runtime and policy group used, are all shown
- you can also view all events as detected by AppDefender in the dashboard
- each event is a observe or deny occurrence as outlined in the section above. Note: grant policies don't generate events
- events are reported by the AppDefender to your dashboard in real time. You can use event reporting to better understand the actions of your functions/applications, as well as inform you on how to better customize your policy groups
- events are kept for different durations depending on your current pricing plan